One way SSL
Introduction
In one-way SSL authentication, the server application shares its public certificate with the client. In a two-way authentication, the client application verifies the identity of the server application, and then the server application verifies the identity of the client application. Sometimes two-way SSL is also known as Mutual Authentication.
In this article, we will be going to learn how to set up the one-way SSL and two-way SSL for MuleSoft applications.
One Way SSL
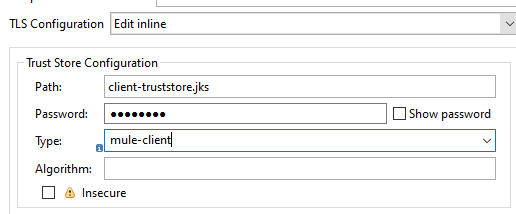
As mentioned above in one way SSL only client verifies the server certificates. At the server end, there will be a Keystore that will hold the private and public certificate of the server whereas, at the client end, there will be a truststore that will hold the public certificate of the server.
Clients will send Hello and request for the resources on the secure HTTPS protocol.
The server will respond with its public certificate (.crt) and send Hello.
The client will verify the server public certificate in its truststore.
The client sends back symmetric session key generated using the server public certificate.
The server will decrypt the symmetric session key using its private certificate and send back the encrypted session key to the client for establishing a secure connection.
Step 1: Generate Server Keystore
keytool -genkey -alias mule-server -keysize 2048 -keyalg RSA -keystore C:/server-keystore.jks

The keystore will be generated in the specified location.
Step 2: Export the Public Certificate From Server Keystore
keytool -export -alias mule-server -keystore C:/server-keystore.jks -file C:/server_public.crt

The public certificate is exported based on the keystore.
Step 3: Import Server Public Certificate Into Client Truststore
keytool -import -alias mule-client-public -keystore C:/client-truststore.jks -file C:/server_public.crt

Step 4: Configuring MuleSoft HTTP Listener and Requester


Now, we will see the client-side configuration. For that, we will be using the MuleSoft HTTP requester. Provide the connection settings on the HTTP requester.
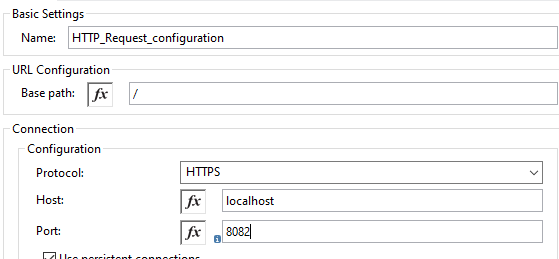
Now, we will do the TLS configuration. Provide the client's truststore path, password, type, etc.